What is this?
I do not know how many times I have looked for an article explaining the just make it work part of how to authenticate to Azure from an application calling an Azure API. I usually find myself in a very long article on scope and OAUTH vs OAUTH2 vs OpenID.
This is more for me as documentation and perhaps for you as well, and it will not go thru why you should configure anything in a particular way. It is just a make it work.
If you do not know how to create an App Registration (necessary for login) or how to get the information used below, I have created a post here.
The three stages of logging in
- Get the information you need.
- Login to get a Token
- Use the Token in an API-call.
Getting the information you need
You will need:
- A Client ID
- A Client Secret
- The Azure Tenant ID
- Know which resource you are using
The 1, 2 and 3
The Client ID and the Tenant ID you can get from the App Registration Overview page of your app.
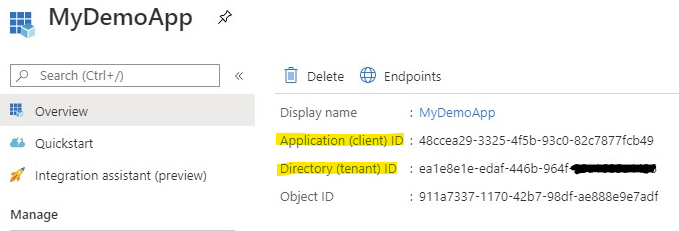
The client secret is either something you previously saved or something you created. Take a look at my post. Click on "Create the App Secret" in the Table of contents at the top if you need more information on how to create a secret.
The resource
This is the only tricky part.
- If you need to manipulate about 90% of Azure you use
https://management.azure.com/ - If you are login into Storage Account you should/could use
https://storage.azure.com/
Postman
The number one client for calling and testing APIs.
Login to get a Token (with Postman)
Gather all the information you have above and lets get to configuring.
You can use variables and environment settings for these.
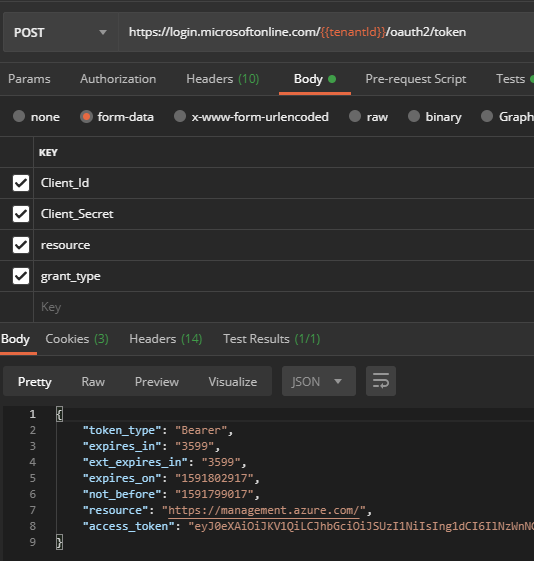
- Set the URI to:
https://login.microsoftonline.com/[Tenant ID Goes here]/oauth2/token - Set the verb to POST.
- Set the format of the body to form-data
- Fill in the data:
client_id: Your Client IDclient_secret: Your client secret (password)resource: see heading just above thisgrant_type: client_credentials
- Click Send and receive your access-token.
Bonus content for Postman
If you want to be fancy, add a script to the test part and assign the token to a local variable for use in other calls.
pm.test(pm.info.requestName, () => { pm.response.to.not.be.error; pm.response.to.not.have.jsonBody('error'); }); pm.environment.set("<your variable>", pm.response.json().access_token);Use the token in the API-call (with Postman)
Now that you have your token, you can use it in other calls.
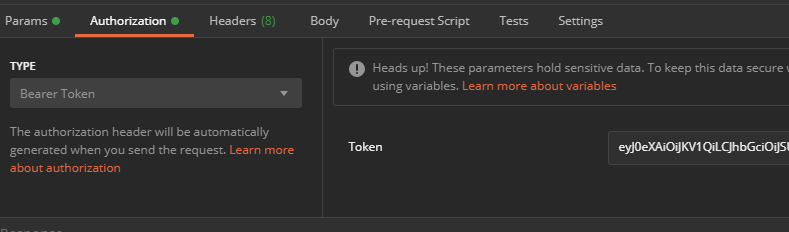
- Simply click Authorization
- In the dropdown select
Bearer Tokenand paste your token in the token-field to the right.
If you used the fancy script, use the variable instead.
- Done!
PowerShell
If clients scare you and you like using scripts to call APIs and execute stuff, you can use PowerShell.
Login to get a token (with PowerShell)
Doing this with PowerShell is even easier, once you know what and how to call stuff, all the code below is located in the same file.
Gather all the information you have above.
# Fill in the data in a collection
authBody = @{
'Client_Id' = 'Your Client ID'
'client_Secret' = 'Your client secret (password)'
'resource' = 'see previous heading about this'
'grant_type' = 'client_credentials'
}tenantId = 'Your Tenant GUID'
# Set the URI
tokenUri = "https://login.microsoftonline.com/(tenantId)/oauth2/token"
# Login to get a Token
# Notice -ContentType and -Formresult = Invoke-RestMethod -Uri tokenUri -ContentType "multipart/form-data" -FormauthBody -Method Post
# A token must be a SecureString when used in later API-calls.
secureToken = ConvertTo-SecureStringresult."access_token" –asplaintext –forceAre you using Windows PowerShell?
If you need to use Windows PowerShell, aka 5.1, you need to replace the Invoke-RestMethod line with:
Invoke-RestMethod -Uri tokenUri -Method Post -BodyauthBodyNote the lack the -Form parameter and -ContentType
Use the token in the API-call (with PowerShell)
When you have your $secureToken you can use it in any API call as a bearer-token.
# Use the token in the API-call
uri = 'https://your api call'response = Invoke-RestMethod -Authentication Bearer -Token secureToken -Uriuri Done!
Bonus content on the Token
Did you know that the Token contains information that you can parse? I sure did not.
Visit eiter https://www.jsonwebtoken.io/ or https://jwt.io/ to see the information in the token. You simply paste your token and see what it contains.
Here is an example of a payload for the token I got in Postman:
{
"aud": "https://management.azure.com/",
"iss": "https://sts.windows.net/<tenantGUID>/",
"iat": 1591799017, <-- Issued At
"nbf": 1591799017, <-- nbf means not before
"exp": 1591802917, <-- The expiration time in Unix timestamp
"aio": "42dgYDhp4Pl5Eccb7me1ixxx",
"appid": "<client ID>",
"appidacr": "1",
"idp": "https://sts.windows.net/<tenantGUID>/",
"oid": "ad049d62-472f-4835-90be-qqqwwwee",
"rh": "0.AQwAHo4e6q_ta0SWTzChaFpEhgeZB<<<<>>>>>.",
"sub": "ad049d62-472f-4835-90be-<<<<>>>>",
"tid": "<tenantGUID>",
"uti": "HZ0eFQf0akCeUE0hJPgjAA",
"ver": "1.0"
}This information can be very useful. The aud (Audiance) should be the same as the resource setting and that might be different in your scenario.
One comment
Comments are closed.